Difference between revisions of "GCube Security Model"
Andrea.turli (Talk | contribs) |
|||
| (40 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | This page describes the security model | + | This page describes the overall security model of gCube. Firstly, the authentication handling is introduced, briefly describing the model and components used by gCube to verify user's identity. Secondly, the authorization section gives a brief description of how the access control is managed in gCube, also introducing main services and components in charge to maintain and enforce authorization policies. |
==Authentication== | ==Authentication== | ||
| − | |||
| − | |||
| − | + | "Authentication is the act of establishing or confirming something (or someone) as authentic, that is, that claims made by or about the subject are true. This might involve confirming the identity of a person, the origins of an artifact, or assuring that a computer program is a trusted one."<ref name="WIKI_AUTHN">http://en.wikipedia.org/wiki/Authentication</ref> | |
| − | + | Being gCube a distributed system, the authentication process mainly focuses on verifying the identity of communicating entities, i.e. users (through the gCube portal), and Running Instances. This is achieved through the use of authentication tokens, i.e. piece of information, that are exchanged between communicating entities to prove their mutual identity. | |
| − | + | '''Delegation''' | |
| − | + | ||
| − | This | + | In short, delegation is the process of letting a system entity, typically a service or an application, to act on behalf of another one, e.g a user. This is normally needed in distributed N-Tier multi-domain applications to take (limited) advantage of privileges grant to the original entity, without the need to directly assign them to the delegated entity<ref name="DELEGATION">http://middleware.internet2.edu/webiso/docs/draft-lajoie-trust_and_delegation-02.html</ref>. Therefore, identity delegation in gCube refers to the process of allowing system services and resources to act on user's behalf. An important point concerning delegation is that, in gCube, services can be dynamically deployed, and autonomously operate in the infrastructure. This implies that a delegation mechanism of user's credentials is required by those services that act in the infrastructure on the user's behalf. |
| − | + | ||
| − | |||
===Model=== | ===Model=== | ||
| − | |||
| + | gCube architecture exploits the '''Public Key Infrastructure'''<ref name="PKI">http://en.wikipedia.org/wiki/Public_key_infrastructure</ref> (PKI) to uniquely identify users and services in the infrastructure. gCube users and services are provided with an authentication token, named credentials, i.e. a private key and a public certificate, that are used to authenticate them to other entities. In PKI, credentials are issued and revoked to users by a trusted entity, named Certification Authority (CA). The gCube infrastructure is designed to support CAs acknowledged by the International Grid Trust Federation<ref name="IGTF">http://www.igtf.net/</ref> (IGTF) as well as an infrastructure-specific CA, named "D4Science CA" in the following. | ||
| + | As from the previous, each interaction between gCube Running Instances, e.g. a service invocation, should be performed in gCube using valid credentials, issued by a trusted Certification Authority (CA). | ||
| − | < | + | As a consequence of this every authenticated communication between gCube entities is performed using valid credentials, issued by a trusted Certification Authority (CA). The main protocol adopted by gCube for secure communications is the '''HTTPS'''<ref name="HTTPS">http://en.wikipedia.org/wiki/HTTP_Secure</ref>: however the ''WS-SecureConversation''<ref name="WS_SEC_CONV">http://specs.xmlsoap.org/ws/2005/02/sc/WS-SecureConversation.pdf</ref>, previously adopted, is still available. The choice of the HTTPS mechanism to protect gCube interactions is mainly due to the better performances provided by HTTPS with respect to message-level security mechanisms. If we use https as only authentication protocol, we will not be able to use the standard delegation mechanism. |
| + | Nevertheless, even considering HTTPS performances, security does not come for free. Sometimes, the overhead introduced in service invocation by the security handshake can take much longer than the invocation itself, thus excessively penalizing the service usability. For this reason, wherever the cost of security was judged too high with respect to advantages introduced, unauthenticated invocations among gCube entities have been allowed also. In those cases, as unauthenticated invocations are performed without valid credentials, neither authentication nor authorization are enforced. | ||
| + | '''Trusted network''' | ||
| − | + | We define as Trusted Network a ''Network of trusted GHN'', where trusted means that their host certificates are signed by a Certification Authority belonging to a specific set. Inside the network the authentication process is simpler. If a call comes from the trusted network (i.e. it is signed by a trusted host certificate), it is considered authenticated: if the specific caller identity is needed (even for delegation purposes), it is provided by roles information used for the authorization process. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | |||
| − | |||
| − | + | ===Components=== | |
| + | Inside the trusted infrastructure there is no need of any specific component, only two features must be present: | ||
| − | + | * the trusted infrastructure CA (or CAs) certificate in the truststore of every GHN | |
| + | * an host certificate signed by (one of) the trusted infrastructure CA. | ||
| + | However a '''Delegation''' and a '''CredentialRenewal''' services are provided when classic delegation is needed. The Delegation service provides gCube services with valid credentials to authenticate themselves in the infrastructure. The provisioning of credentials to services operated by the Delegation depends on service security configuration, being the use of container credentials the most common, and simple, case. For services requiring to act on the user behalf, the Delegation interacts with the Credentials Renewal service to retrieve delegated user's credentials. The delegation of user's credentials to a service is subject to a defined set of delegation policies. | ||
| − | + | A more detailed description of the structure and behaviour of the authentication-related components can be found in the [[Virtual Organisation Management]] page. | |
| + | ==Authorization == | ||
| + | "Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy. For example, Human Resources staff are normally authorized to access employee records, and this policy is usually formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be granted or rejected."<ref name="WIKI_AUTHZ">http://en.wikipedia.org/wiki/Authorization</ref>. | ||
| − | + | Authorization rights in gCube are based upon the '''Role Based Access Control'''<ref name="RBAC">http://en.wikipedia.org/wiki/Role-Based_Access_Control</ref>(RBAC) model. In RBAC, each identity is associated to one or more attributes, named roles, that are, in turn, linked to permissions granted to the role itself. This allows for a more flexible management of permissions, with respect to mandatory access control (MAC) and discretionary access control (DAC), that directly link permissions to identities. | |
| − | + | As a consequence, gCube users must held a role to operate in the gCube infrastructure. In particular authorization policies in the system are defined with respect to roles, that, in turn, are assigned to users. Each resource is then in charge to enforce authorization policies on incoming requests. | |
| − | + | ||
| − | + | ||
| − | + | In distributed, multi-domain systems the term '''Virtual Organisation''' (VO) refers to virtual environments spanning across different administrative domains<ref name="VO_REPORT">http://www.ci.uchicago.edu/events/VirtOrg2008/VO_report.pdf</ref>. gCube architecture mainly aims at enabling Virtual Research Environments, and for this reason Virtual Organizations are a core concept of GCube. In particular, when it comes to authorization, the RBAC model must be merged to the sharing of resources typically enabled in the context of a VO. | |
| − | [[Image: | + | ===Model=== |
| + | The definition and management of access policies for gCube resources is a process involving two main actors: | ||
| + | |||
| + | * '''Resource Administrators''': these actors are the owners of resources. They have the ultimate control over resource usage. They defines Sharing Rules, ruling the usage of their resources over Virtual Organization. | ||
| + | * '''VO Administrators''': these actors are in charge of define Permissions, describing how a resource, made available to the VO by a Resource Administrator, can be used by Users. | ||
| + | |||
| + | The following diagram shows main elements of the VO authorisation model of gCube. In particular, authorisation policies in gCube are scope specific, being the scope concept defined in the [[Reference_Model|gCube reference model]]. It is worth noticing that each scope of the gCube reference model corresponds to a Virtual Organisation in the following model. | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | <center>[[Image:VO_Model.jpg|500px]]</center> | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | Each element in the diagram is briefly introduced below: | ||
| + | * '''VO''': Each VO in the hierarchy represent a context in which authorization policies are defined and evaluated. | ||
| + | * '''User''': Users of the gCube system. Every user will be univocally identified using a set of user credentials as described in the Authentication section above. Users can be part of more than one VO. | ||
| + | * '''Resource''': This element represents the set of gCube resources. Each resource is identified through a resource id, unique in the gCube infrastructure. Resources can be included in more than one VO. | ||
| + | * '''Operation''': Operations represents actions that can be performed on resources. Each operation is identified by an id that is unique among those of operations available on resources of a given class. | ||
| + | * '''Sharing Rule''': These policies are defined by Resource Administrators to grant a VO access to a given resource. Sharing rules applies to VO as a whole. | ||
| + | * '''Permission''': Permissions are defined by VO Administrators to grant the right to perform operations, described by Sharing Rules, to users with a specific role in the VO. Worth noticing that Permissions are defined starting to Sharing Rules and cannot be less restrictive of Sharing Rules they derives from. | ||
| + | * '''Role''': Roles are associated to users in order to grant them the associated set of permissions. Roles in the gCube authorisation model are associated to users in the context of a given scope. | ||
| − | + | Policy enforcement is performed by resources contacting the authorization components, described below, and verifying that the operation asked by the client complies with the set of defined policies (Sharing Rules and Permissions). The '''push authorization model''' is used to enforce authorization for gCube resources<ref name="AUTHZ_MODELS">http://www.ogf.org/documents/GFD.38.pdf</ref>. In our trusted network a piece of information containing the role is added by the Trusted Node. The receiver Node extracts that piece of information and checks if the caller role is authorized to perform the required action. This operation is performed with the aid of the ''Authorization Service'' | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ===Components=== | |
| − | + | In the trusted network Authorization Control is performed by a particular element of the architecture: the '''Authorization Service'''. It is composed by two modules: | |
| − | * | + | * '''Policy Administration Point''' ('''PAP'''), in which policies, written in a particular syntax, are stored |
| − | * | + | * '''Policy Decision Pount''' ('''PDP'''), which computes the policies against a certain request and communicates a result, that could be a ''Permit'', a ''Deny'' or an ''Indeterminate''. |
| − | + | ||
| − | + | A third component, the '''Policy Enforcement Point''' ('''PEP''') is represented by the Node that is responsible to apply the decision of the associated PDP. In case of Indeterminate decision the PEP denies the request. | |
| − | + | The '''VOMS''' is used only for gLite interoperability purpose. In gCube, a VOMS<ref name="VOMS">http://grid-auth.infn.it/</ref> server maintains the scope hierarchy as a groups hierarchy in a dedicated VOMS VO. It is also in charge to store the set of gCube users, as well as their group membership and roles assigned to them. Finally, VOMS is in charge to release signed Attribute Certificates stating user privileges (group membership and roles held). | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | A more detailed description of the structure and behaviour of the authorization-related components can be found in the [[Virtual Organisation Management]] page. | |
| − | + | == References == | |
| + | <references/> | ||
[[Category:Security]] | [[Category:Security]] | ||
Latest revision as of 14:19, 14 July 2011
This page describes the overall security model of gCube. Firstly, the authentication handling is introduced, briefly describing the model and components used by gCube to verify user's identity. Secondly, the authorization section gives a brief description of how the access control is managed in gCube, also introducing main services and components in charge to maintain and enforce authorization policies.
Contents
Authentication
"Authentication is the act of establishing or confirming something (or someone) as authentic, that is, that claims made by or about the subject are true. This might involve confirming the identity of a person, the origins of an artifact, or assuring that a computer program is a trusted one."[1]
Being gCube a distributed system, the authentication process mainly focuses on verifying the identity of communicating entities, i.e. users (through the gCube portal), and Running Instances. This is achieved through the use of authentication tokens, i.e. piece of information, that are exchanged between communicating entities to prove their mutual identity.
Delegation
In short, delegation is the process of letting a system entity, typically a service or an application, to act on behalf of another one, e.g a user. This is normally needed in distributed N-Tier multi-domain applications to take (limited) advantage of privileges grant to the original entity, without the need to directly assign them to the delegated entity[2]. Therefore, identity delegation in gCube refers to the process of allowing system services and resources to act on user's behalf. An important point concerning delegation is that, in gCube, services can be dynamically deployed, and autonomously operate in the infrastructure. This implies that a delegation mechanism of user's credentials is required by those services that act in the infrastructure on the user's behalf.
Model
gCube architecture exploits the Public Key Infrastructure[3] (PKI) to uniquely identify users and services in the infrastructure. gCube users and services are provided with an authentication token, named credentials, i.e. a private key and a public certificate, that are used to authenticate them to other entities. In PKI, credentials are issued and revoked to users by a trusted entity, named Certification Authority (CA). The gCube infrastructure is designed to support CAs acknowledged by the International Grid Trust Federation[4] (IGTF) as well as an infrastructure-specific CA, named "D4Science CA" in the following.
As from the previous, each interaction between gCube Running Instances, e.g. a service invocation, should be performed in gCube using valid credentials, issued by a trusted Certification Authority (CA).
As a consequence of this every authenticated communication between gCube entities is performed using valid credentials, issued by a trusted Certification Authority (CA). The main protocol adopted by gCube for secure communications is the HTTPS[5]: however the WS-SecureConversation[6], previously adopted, is still available. The choice of the HTTPS mechanism to protect gCube interactions is mainly due to the better performances provided by HTTPS with respect to message-level security mechanisms. If we use https as only authentication protocol, we will not be able to use the standard delegation mechanism.
Nevertheless, even considering HTTPS performances, security does not come for free. Sometimes, the overhead introduced in service invocation by the security handshake can take much longer than the invocation itself, thus excessively penalizing the service usability. For this reason, wherever the cost of security was judged too high with respect to advantages introduced, unauthenticated invocations among gCube entities have been allowed also. In those cases, as unauthenticated invocations are performed without valid credentials, neither authentication nor authorization are enforced.
Trusted network
We define as Trusted Network a Network of trusted GHN, where trusted means that their host certificates are signed by a Certification Authority belonging to a specific set. Inside the network the authentication process is simpler. If a call comes from the trusted network (i.e. it is signed by a trusted host certificate), it is considered authenticated: if the specific caller identity is needed (even for delegation purposes), it is provided by roles information used for the authorization process.
Components
Inside the trusted infrastructure there is no need of any specific component, only two features must be present:
- the trusted infrastructure CA (or CAs) certificate in the truststore of every GHN
- an host certificate signed by (one of) the trusted infrastructure CA.
However a Delegation and a CredentialRenewal services are provided when classic delegation is needed. The Delegation service provides gCube services with valid credentials to authenticate themselves in the infrastructure. The provisioning of credentials to services operated by the Delegation depends on service security configuration, being the use of container credentials the most common, and simple, case. For services requiring to act on the user behalf, the Delegation interacts with the Credentials Renewal service to retrieve delegated user's credentials. The delegation of user's credentials to a service is subject to a defined set of delegation policies.
A more detailed description of the structure and behaviour of the authentication-related components can be found in the Virtual Organisation Management page.
Authorization
"Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy. For example, Human Resources staff are normally authorized to access employee records, and this policy is usually formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be granted or rejected."[7].
Authorization rights in gCube are based upon the Role Based Access Control[8](RBAC) model. In RBAC, each identity is associated to one or more attributes, named roles, that are, in turn, linked to permissions granted to the role itself. This allows for a more flexible management of permissions, with respect to mandatory access control (MAC) and discretionary access control (DAC), that directly link permissions to identities.
As a consequence, gCube users must held a role to operate in the gCube infrastructure. In particular authorization policies in the system are defined with respect to roles, that, in turn, are assigned to users. Each resource is then in charge to enforce authorization policies on incoming requests.
In distributed, multi-domain systems the term Virtual Organisation (VO) refers to virtual environments spanning across different administrative domains[9]. gCube architecture mainly aims at enabling Virtual Research Environments, and for this reason Virtual Organizations are a core concept of GCube. In particular, when it comes to authorization, the RBAC model must be merged to the sharing of resources typically enabled in the context of a VO.
Model
The definition and management of access policies for gCube resources is a process involving two main actors:
- Resource Administrators: these actors are the owners of resources. They have the ultimate control over resource usage. They defines Sharing Rules, ruling the usage of their resources over Virtual Organization.
- VO Administrators: these actors are in charge of define Permissions, describing how a resource, made available to the VO by a Resource Administrator, can be used by Users.
The following diagram shows main elements of the VO authorisation model of gCube. In particular, authorisation policies in gCube are scope specific, being the scope concept defined in the gCube reference model. It is worth noticing that each scope of the gCube reference model corresponds to a Virtual Organisation in the following model.
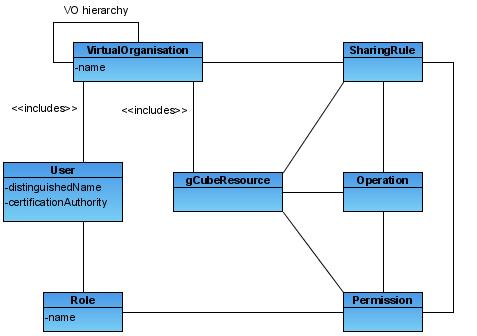
Each element in the diagram is briefly introduced below:
- VO: Each VO in the hierarchy represent a context in which authorization policies are defined and evaluated.
- User: Users of the gCube system. Every user will be univocally identified using a set of user credentials as described in the Authentication section above. Users can be part of more than one VO.
- Resource: This element represents the set of gCube resources. Each resource is identified through a resource id, unique in the gCube infrastructure. Resources can be included in more than one VO.
- Operation: Operations represents actions that can be performed on resources. Each operation is identified by an id that is unique among those of operations available on resources of a given class.
- Sharing Rule: These policies are defined by Resource Administrators to grant a VO access to a given resource. Sharing rules applies to VO as a whole.
- Permission: Permissions are defined by VO Administrators to grant the right to perform operations, described by Sharing Rules, to users with a specific role in the VO. Worth noticing that Permissions are defined starting to Sharing Rules and cannot be less restrictive of Sharing Rules they derives from.
- Role: Roles are associated to users in order to grant them the associated set of permissions. Roles in the gCube authorisation model are associated to users in the context of a given scope.
Policy enforcement is performed by resources contacting the authorization components, described below, and verifying that the operation asked by the client complies with the set of defined policies (Sharing Rules and Permissions). The push authorization model is used to enforce authorization for gCube resources[10]. In our trusted network a piece of information containing the role is added by the Trusted Node. The receiver Node extracts that piece of information and checks if the caller role is authorized to perform the required action. This operation is performed with the aid of the Authorization Service
Components
In the trusted network Authorization Control is performed by a particular element of the architecture: the Authorization Service. It is composed by two modules:
- Policy Administration Point (PAP), in which policies, written in a particular syntax, are stored
- Policy Decision Pount (PDP), which computes the policies against a certain request and communicates a result, that could be a Permit, a Deny or an Indeterminate.
A third component, the Policy Enforcement Point (PEP) is represented by the Node that is responsible to apply the decision of the associated PDP. In case of Indeterminate decision the PEP denies the request.
The VOMS is used only for gLite interoperability purpose. In gCube, a VOMS[11] server maintains the scope hierarchy as a groups hierarchy in a dedicated VOMS VO. It is also in charge to store the set of gCube users, as well as their group membership and roles assigned to them. Finally, VOMS is in charge to release signed Attribute Certificates stating user privileges (group membership and roles held).
A more detailed description of the structure and behaviour of the authorization-related components can be found in the Virtual Organisation Management page.
References
- ↑ http://en.wikipedia.org/wiki/Authentication
- ↑ http://middleware.internet2.edu/webiso/docs/draft-lajoie-trust_and_delegation-02.html
- ↑ http://en.wikipedia.org/wiki/Public_key_infrastructure
- ↑ http://www.igtf.net/
- ↑ http://en.wikipedia.org/wiki/HTTP_Secure
- ↑ http://specs.xmlsoap.org/ws/2005/02/sc/WS-SecureConversation.pdf
- ↑ http://en.wikipedia.org/wiki/Authorization
- ↑ http://en.wikipedia.org/wiki/Role-Based_Access_Control
- ↑ http://www.ci.uchicago.edu/events/VirtOrg2008/VO_report.pdf
- ↑ http://www.ogf.org/documents/GFD.38.pdf
- ↑ http://grid-auth.infn.it/