Difference between revisions of "Argus Installation"
(→Introduction) |
|||
| (3 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| + | [[Category:Administrator's Guide]] | ||
==Introduction== | ==Introduction== | ||
Argus Authorization Framework<ref name="Argus_Site">https://twiki.cern.ch/twiki/bin/view/EGEE/AuthorizationFramework</ref> is an implementation of OASIS ''eXtended Access Control Markup Language'' (XACML) Standard<ref>http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf</ref>. It is composed by a set of web services provided by three elements: | Argus Authorization Framework<ref name="Argus_Site">https://twiki.cern.ch/twiki/bin/view/EGEE/AuthorizationFramework</ref> is an implementation of OASIS ''eXtended Access Control Markup Language'' (XACML) Standard<ref>http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf</ref>. It is composed by a set of web services provided by three elements: | ||
| Line 12: | Line 13: | ||
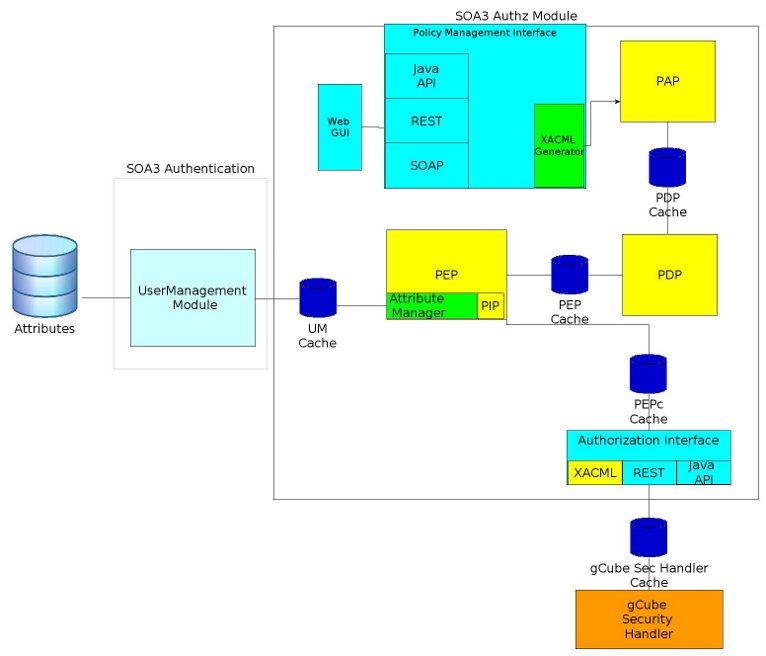
The picture shows how Argus elements is integrated in SOA3 Authorization Module: in particular, [[SOA3 Policy Management Service]] manages the policies with Argus PAP, while the PEPC library is integrated in [[SOA3 Authorization Service]] and communicates with Argus PEPD. | The picture shows how Argus elements is integrated in SOA3 Authorization Module: in particular, [[SOA3 Policy Management Service]] manages the policies with Argus PAP, while the PEPC library is integrated in [[SOA3 Authorization Service]] and communicates with Argus PEPD. | ||
| − | In this section a step by step guide to configure Argus elements is provided: it is based on Argus 1.5.0, but other versions differs only for the path of the configuration files. | + | In this section a step by step guide to configure Argus elements is provided: it is based on Argus 1.5.0, but other versions differs only for the path of the configuration files. The installation procedure has been tested on ''Centos 6.4'' and ''Fedora 17'', but it should be valid for any Red Hat based distribution and for any linux distribution supporting RPMs. |
| + | |||
| + | Argus v1.5.0 or above is recommended: an RPM can be found [https://i-marine.d4science.org/group/data-e-infrastructure-gateway/workspace?itemid=03dcbd8a-98b9-4eb6-b409-bfbfa95dd13d here]. | ||
==Policy Administration Point== | ==Policy Administration Point== | ||
| Line 31: | Line 34: | ||
</source> | </source> | ||
| − | <code>role.xacml-match-function</code> | + | <code>role.xacml-match-function</code> establishes that the match must be performed using regexp: in this case rules based on roles defined by regular expressions are supported. |
It is possible to add other subject attributes, e.g.: | It is possible to add other subject attributes, e.g.: | ||
| Line 76: | Line 79: | ||
* ''hostname'' with the correct name (with dns suffix) of the host | * ''hostname'' with the correct name (with dns suffix) of the host | ||
* ''security section'', in particular ''certificate'' and ''private_key'' with the path to the TLS certificate and key | * ''security section'', in particular ''certificate'' and ''private_key'' with the path to the TLS certificate and key | ||
| − | |||
==Policy Decision Point== | ==Policy Decision Point== | ||
Latest revision as of 18:18, 27 January 2014
Contents
Introduction
Argus Authorization Framework[1] is an implementation of OASIS eXtended Access Control Markup Language (XACML) Standard[2]. It is composed by a set of web services provided by three elements:
- Policy Administration Point (PAP), to store and manage XACML Policies
- Policy Decision Point (PDP), to take authorization decision basing on the policies and context attributes (e.g. date/hour)
- Policy Enforcement Point, Client (PEPC) and Daemon (PEPD), to enforce policy decisions
Further information on the architecture can be found on SOA3 Authorization Module.
The picture shows how Argus elements is integrated in SOA3 Authorization Module: in particular, SOA3 Policy Management Service manages the policies with Argus PAP, while the PEPC library is integrated in SOA3 Authorization Service and communicates with Argus PEPD.
In this section a step by step guide to configure Argus elements is provided: it is based on Argus 1.5.0, but other versions differs only for the path of the configuration files. The installation procedure has been tested on Centos 6.4 and Fedora 17, but it should be valid for any Red Hat based distribution and for any linux distribution supporting RPMs.
Argus v1.5.0 or above is recommended: an RPM can be found here.
Policy Administration Point
The file
/etc/argus/pap/attribute-mappings.ini
contains the attributes recognized by argus. For IMarine it should contain at least roles:
id = role role.xacml-id = urn:oasis:names:tc:xacml:2.0:subject:role role.xacml-datatype = http://www.w3.org/2001/XMLSchema#string role.xacml-target-element = subject role.xacml-match-function = urn:oasis:names:tc:xacml:1.0:function:string-regexp-match
role.xacml-match-function establishes that the match must be performed using regexp: in this case rules based on roles defined by regular expressions are supported.
It is possible to add other subject attributes, e.g.:
id = subject subject.xacml-id = urn:oasis:names:tc:xacml:1.0:subject:subject-id subject.xacml-datatype = http://www.w3.org/2001/XMLSchema#string subject.xacml-target-element = subject subject.xacml-match-function = urn:oasis:names:tc:xacml:1.0:function:string-equal id = tenant tenant.xacml-id = urn:oasis:names:tc:xacml:2.0:subject:tenant tenant.xacml-datatype = http://www.w3.org/2001/XMLSchema#string tenant.xacml-target-element = subject tenant.xacml-match-function = urn:oasis:names:tc:xacml:1.0:function:string-regexp-match
Action and resource attributes defined for IMarine are the following:
id = action action.xacml-id = urn:oasis:names:tc:xacml:1.0:action:action-id action.xacml-datatype = http://www.w3.org/2001/XMLSchema#string action.xacml-target-element = action action.xacml-match-function = urn:oasis:names:tc:xacml:1.0:function:string-regexp-match id = resource resource.xacml-id = urn:oasis:names:tc:xacml:1.0:resource:resource-id resource.xacml-datatype = http://www.w3.org/2001/XMLSchema#string resource.xacml-target-element = resource resource.xacml-match-function = urn:oasis:names:tc:xacml:1.0:function:string-regexp-match
The file
/etc/argus/pap/pap_configuration_ini
is the main configuration file for Argus PAP. The parameters to be modified are the following:
- hostname with the correct name (with dns suffix) of the host
- security section, in particular certificate and private_key with the path to the TLS certificate and key
Policy Decision Point
The configuration file is the following:
/etc/argus/pdp/pdp.ini
and the parameters to be modified are:
- hostname and adminHost: hostname (with dns suffix) of the machine
- paps: the url(s) of the policy provisioning service(s) provided by the PAP(s). The pattern is https://<pap-hostname>:<pap-port>/pap/services/ProvisioningService: comma separated values are supported
- security section
- enableSSL (true/false) to enable https protocol (recommended)
- servicePrivateKey path of the private key
- serviceCertificate path of the public key
- trustInfoDir path of the directory containing the trusted CA for client authentication
Policy Enforcement Point Daemon
The configuration file is
/etc/argus/pepd/pepd.ini
and the parameters to be modified are:
- hostname with the correct name (with dns suffix) of the host
- pips should be TIME_PIP to enable time based policies
- pdps: the url(s) of the policy decision service(s). The pattern is https://<pdp-hostname>:<pap-port>:8152/authz: comma separated values are supported
- security section
- servicePrivateKey path of the private key
- serviceCertificate path of the public key
- trustInfoDir path of the directory containing the trusted CA for client authentication
- enableSSL (true/false) to enable https protocol (recommended)
- requireClientCertAuthentication (true/false) to enable client ssl authentication (recommended)