Difference between revisions of "Auth Portlet"
(→Insert a Policy) |
(→Introduction) |
||
| Line 5: | Line 5: | ||
==Introduction== | ==Introduction== | ||
| − | With this portlet it’s possible to create a policy to deny access to | + | With this portlet it’s possible to create a policy to deny access to the service in the current context. |
''Below it is shown the overall layout of the Auth Portlet'' | ''Below it is shown the overall layout of the Auth Portlet'' | ||
Revision as of 21:59, 4 October 2016
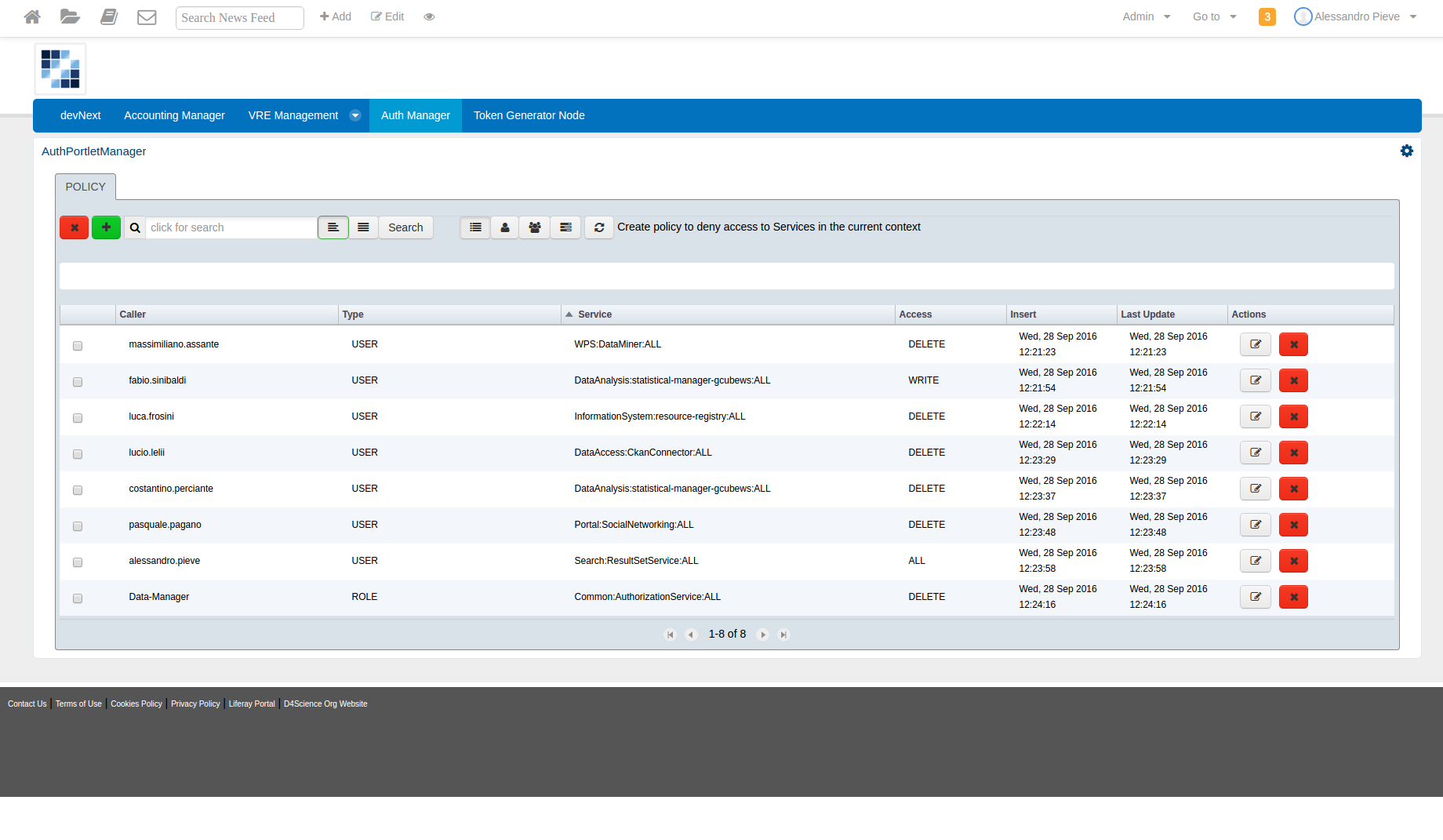
Introduction
With this portlet it’s possible to create a policy to deny access to the service in the current context.
Below it is shown the overall layout of the Auth Portlet
Every policy is consisting of:
- one or more Caller
- Service
- Access
The caller can be an User, a Role or a Service and you can insert one or more callers for each policy.
(The insertion of a policy with more callers results as more policy).
The service is specified as service class, service name and service id.
The access that we want to deny can be:
- All
- Access
- Delete
- Execute
- Write
Insert/Modify a Policy
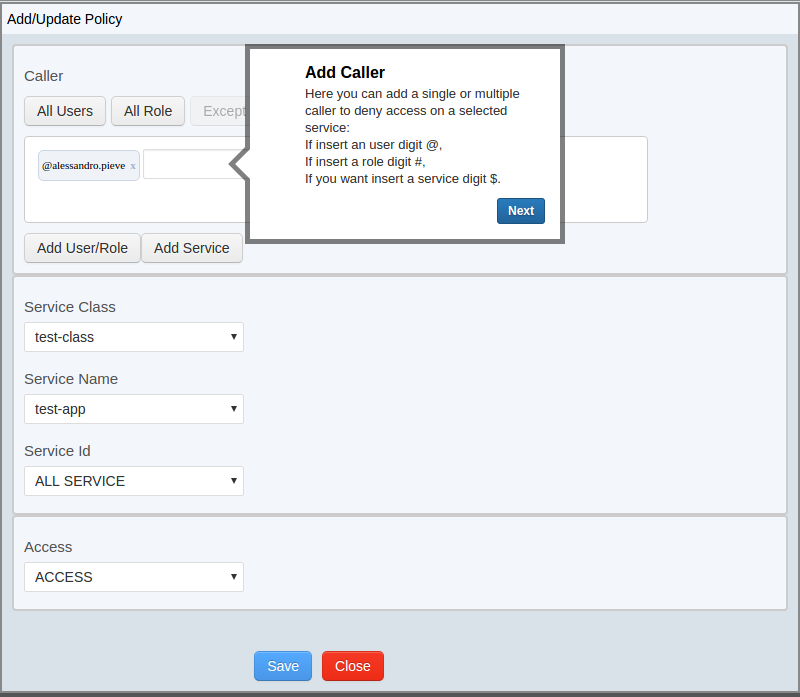
For insert a policy we can add one or more Caller, one service and access type.
The insertion of a caller can be made with an autocomplete writing in the input, or clicking the button Add User role or add service, that opens a pop-up to insert more things.
We can create a policy that inserts all users or all role with the specific button “All Users” or “All Role”
The insertion of a caller can be made with complete input text , or clicking button “Add User/ Role” or “Add Service” to open a pop up for multiple entry.
The insertion with an autocomplete can be made with the insertion of a first controlled character:
- if you insert a user, you can digit @ for see all users
- if you insert a role, you can digit # for see all roles
- if you want insert a service, you can digit $ for see all the services.
The selection of the service and the access type It’s done with a selected dropdown
We can insert a policy that allows the use of a service only to one or more caller, selecting the combination ALL Users/All role and Except.
In this case, the callers, entered in input text, are enabled to access a service.
For an existing policy, you can change only the service and the access type.
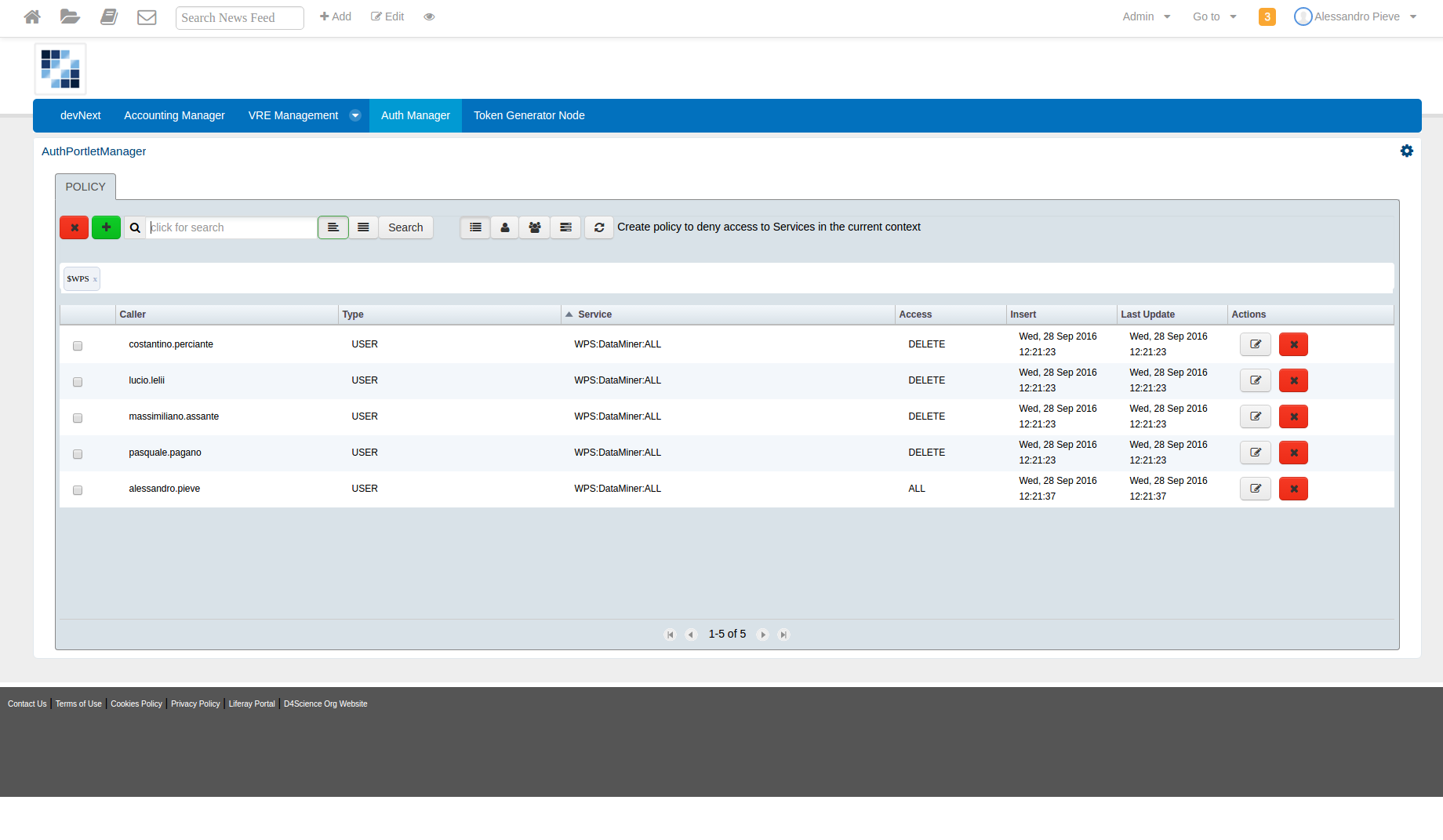
Search a Policy
It Is possible search, filter and group by all policy.
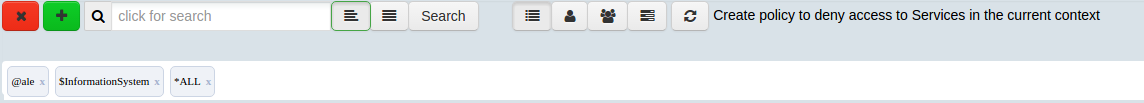
If we want to search a caller, we can digit @ before inserting a name of the caller.
If we want to search a service, we can digit $ before inserting a name of the service.
And finally if we want to search an access, we can digit * before inserting a type of an access.
The filter can be incremental.
Over the filter we can organize a policy in caller type, for example user, role and service
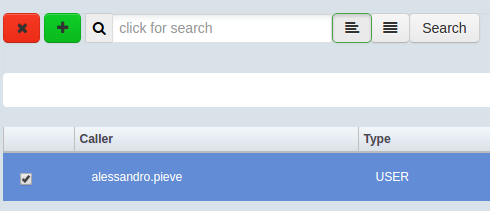
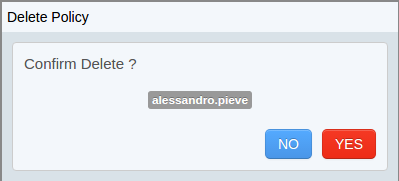
Delete a Policy
It’s possible to delete one or more policies simply clicking on the delete button.