GeoNetwork Configuration
GeoNetwork is a catalog application to manage spatially referenced resources, thus is a strategic technology for all geospatial application. Purpose of this page is to explain how to configure a GeoNetwork service instance in order to fulfill the needs of gCube environment. Please refer to its official website for further configuration details and more comprehensive documentation.
Contents
Installation
GeoNetwork version adopted by the gCube infrastructure is 2.6.4 , available here.
Prerequisites are :
- java 5+
- apache tomcat 5+
- postgres 7+
SmartGears Installation
In order to enable SmartGears to correctly handle the web application, the following values must be declared in its gcube-app.xml file :
- Name : GeoNetwork
- Group : SDI
- Description : OGC compliant catalog by geosolutions
The following SmartGears handlers should be excluded :
- request-validation
Database configuration
In order to configure GeoNetwork to use postgis jdbc connection to the local database, the file config.xml under $TOMCAT_HOME/webapps/geonetwork/WEB-INF must be properly edited. A development config.xml file copy is provided in shared workspace folder https://goo.gl/dros0u. Just change the postgres connection parameters of the provided file once copied to the webapp. Please, note that the jdbc url to the database must have the form jdbc:postgis://<HOST>:<PORT>/<DATABASE_NAME>, otherwise the spatial metadata catalog is created as a shapefile, which may cause a loss of performance (please refer to official documentation for further information).
Security in gcube 3.X
To reproduce visibility and security means of the gCube infrastructure, the security module of GeoNetwork need to be configured accordingly to the scope(s) in which it is registered in. Please note that the following conventions needs to be maintained according to the infrastructure state.
Groups
For each scope in which the GeoNetwork instance is registered in, the administrator must create a group with the same name of the scope.
I.e. Let's assume our instance to be registered both in d4science.research-infrastructures.eu and in d4science.research-infrastructures.eu/gCubeApps. The GeoNetwork must be configured with at least the 2 groups d4science.research-infrastructures.eu and gCubeApps.
Users
Other then at least one administrator user, 2 users must be set for each and every scope in which the GeoNetwork is registered. The convention for these users name is :
- <SCOPE>_Public : used to publish / read metadata with a scope level visibility. Role of this user must be set as Editor for the groups in which it must have read access (The <SCOPE> group itself and every sub scope in case of VO or INFRASTRUCTURE);
- <SCOPE>_Private : used to publish / read metadata with a private visibility. Role of this user must be set as as Editor for its <SCOPE> group.
For more clarity, let's say our GeoNetwork service is registered in d4science.research-infrastructures.eu/gCubeApps and in d4science.research-infrastructures.eu/gCubeApps/EcoligicalModelling scopes. As stated above in the group section, our service is supposed to be configured with at least the groups gCubeApps and EcologicalModelling. With these assumptions, these are the expected users :
- Administrator : user with administrator role
- gCubeApps_Private : Editor role in the group gCubeApps
- gCubeApps_Public : Editor role in the groups gCubeApps and EcologicalModelling
- EcologicalModelling_Private : Editor role in the group EcologicalModelling
- EcologicalModelling_Public : Editor role in the group EcologicalModelling
Security in gcube 4.X
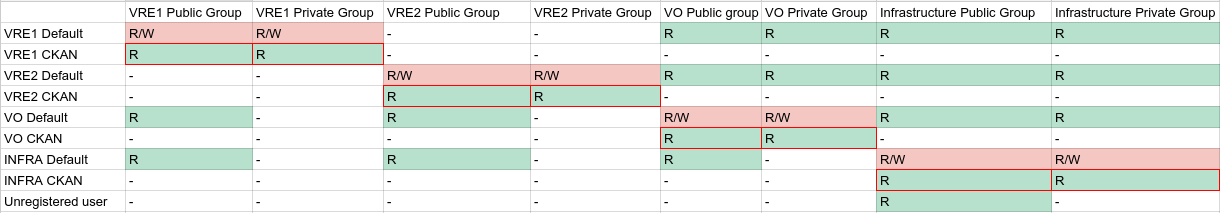
Access rights table
The following schema report the publish/visibility policies to be followed from gcube 4.0.0.
Scope Configuration
Please note that the library org.gcube.spatial.data.geonetwork automatically creates a scope configuration if none is already setup, both updating Information system and GeoNetwork master instance. For completeness we report here groups and users involved in each scope configuration :
- Private_Group : Group with visibility only from the current scope or enclosed ones (ie : VRE_SCOPE_USER can access it's VO_PRIVATE_GROUP);
- Public_Group : Group with visibility only from the current scope and enclosing ones (ie : VO_SCOPE_USER can access it's VRE_PUBLIC_GROUP);
- Scope_User : Editor user in GeoNetwork, with rights in current scope groups and enclosing ones;
- CKAN_User : Registered user in GeoNetwork, with rights in current scope groups.
GeoNetwork categories
External resources
External OGC catalogs are managed via the harvesting facility offered by GeoNetwork. Please read the related documentation on the provider's official page.
GUI Customization
Replica management
To improve robustness, reliability and performance of the SDI, one or more replica of a GeoNetwork service can be registered in a given scope. These instances must be registered with the boolean flag master as false. See [Runtime Resource] below for more details.
Runtime Resource
The Geo Network Runtime Resource gives information about Geo Network instance deployed: where the Geo Network is deployed and what are the credentials to contact it.
Description
There will be one Runtime Resource for each Geo Network instance.
The resource can be registered:
- at VO level, if the Geo Network instance is shared between VREs.
- at VRE level, if the Geo Network instance is VRE dedicated.
The Geo Network runtime resource is mandatory if in the VO/VRE are installed application using the GCube Gis Viewer widget.
Fields
The following Runtime Resource standard fields value are mandatory in order to discover it in the infrastructure :
- Category = Gis
- Platform/Name = geonetwork
Other than required Runtime Resource fields almost one access point is needed with the following constraints :
- Endpoint EntryName = geonetwork
- boolean property master
- For each gCube scope (indicated as <SCOPE_NAME>) in which the Runtime Resource is registered, the access point should declare the following properties
- encrypted string property <SCOPE_NAME>_Public containing the password of the public user for the given scope
- encrypted string property <SCOPE_NAME>_Private containing the password of the private user for the given scope
- integer property <SCOPE_NAME>_group containing the id of the publishing group for the given scope
Example
<Resource version="0.4.x"> <ID>b7fce5e0-b0e5-11e2-9d26-c9dc2c525e1c</ID> <Type>RuntimeResource</Type> <Scopes> <Scope>/gcube/devNext</Scope> </Scopes> <Profile> <Category>Gis</Category> <Name>GeoNetwork</Name> <Description /> <Platform> <Name>geonetwork</Name> <Version>2</Version> <MinorVersion>2</MinorVersion> <RevisionVersion>2</RevisionVersion> <BuildVersion>2</BuildVersion> </Platform> <RunTime> <HostedOn>geoserver-dev2.d4science-ii.research-infrastructures.eu</HostedOn> <GHN UniqueID="" /> <Status>READY</Status> </RunTime> <AccessPoint> <Description>Main access point</Description> <Interface> <Endpoint EntryName="geonetwork">http://geoserver-dev2.d4science-ii.research-infrastructures.eu/geonetwork</Endpoint> </Interface> <AccessData> <Username>admin</Username> <Password>wW9T5/k5VaLdTdc3WlPbWw==</Password> </AccessData> <Properties> <Property> <Name>devNext_group</Name> <Value encrypted="false">7</Value> </Property> <Property> <Name>devNext_Private</Name> <Value encrypted="true">Jm3d1N30c2gCjjo828IdOw==</Value> </Property> <Property> <Name>devNext_Public</Name> <Value encrypted="true">5I/EJznPaq3flojA4HTz5Q==</Value> </Property> <Property> <Name>master</Name> <Value encrypted="false">true</Value> </Property> </Properties> </AccessPoint> </Profile> </Resource>