Difference between revisions of "GCube Security Model"
Andrea.turli (Talk | contribs) |
|||
| Line 1: | Line 1: | ||
| − | This page describes the security model | + | This page describes the overall security model of gCube. Firstly, the authentication handling is introduced, briefly describing the model and components used by gCube to verify user's identity. Secondly, the authorization section gives a brief description of the gCube model, also highlighting main services and components in charge to maintain and enforce authorization policies. |
==Authentication== | ==Authentication== | ||
| − | |||
| − | |||
| − | + | "Authentication is the act of establishing or confirming something (or someone) as authentic, that is, that claims made by or about the subject are true. This might involve confirming the identity of a person, the origins of an artifact, or assuring that a computer program is a trusted one."<ref name="WIKI_AUTHN">http://en.wikipedia.org/wiki/Authentication</ref> | |
| − | + | Being gCube a distributed system, the authentication process mainly focuses on proving the identity of communicating entities (users, services, hosts, etc.). The aim of gCube authentication is mainly to prevent system usage or damaging by malcious entities. | |
| − | === | + | ==== Delegation ==== |
| − | + | ||
| − | + | "In numerous applications it is sometimes necessary to "become" some one else, or some other principal in order to take advantage of some privilege(s) they have. Unix systems have had this concept for decades in the su command. With the advent of web based enterprise applications it became clear that something similar was needed for them. That is it became necessary to be able to pass around a set of privileges in some manner. Since privileges are normally associated with a principal (very often a person) the problem became a question of how to pass around these principal's identities and how to allow one system to use that identity to gain access to information on another system."<ref name="DELEGATION">http://middleware.internet2.edu/webiso/docs/draft-lajoie-trust_and_delegation-02.html</ref> | |
| − | + | ||
| + | As from the previous excerpt, identity delegation in gCube is the process of allowing system services and resources to act on user's behalf. This functionality is often required in N-tier large-scale systems, like gCube. An important point to be taken into account when considering delegation is that gCube service can be dynamically deployed in the infrastructure, even if the service administator is not logged in. Even in those cases, valid credentials must be delegated to the deployed service in order to properly operate in the gCube infrastructure. | ||
| − | |||
===Model=== | ===Model=== | ||
| − | |||
| + | gCube architecture exploits the Public Key Infrastructure<ref name="PKI">http://en.wikipedia.org/wiki/Public_key_infrastructure</ref> (PKI) paradigm to uniquely identify users in the infrastructure. gCube users are then provided with a set of credentials, i.e. a private key and a public certificate, that are used to for authentication to other entities. Credentials are typically issued and revoked to users by a trusted entity, named Certification Authority (CA). The gCube infrastructure is designed to support CAs acknowledged by the International Grid Trust Federation<ref name="IGTF">http://www.igtf.net/</ref> (IGTF) as well as an infrastructure-specific CA, named "D4Science CA" in the following of this section. | ||
| + | As from the previous, each interaction between entitites, e.g. a service invocation, should be performed in gCube using valid credentials, issued by a trusted Certification Authority (CA). | ||
| − | + | As far as performances are concerned, security does not come for free. Sometimes the overhead introduced in service invocation by the security handshake can take much longer than the invocation itself, thus excessively penalizing service usability. For this reason also unauthenticated invocatons among gCube entities have been allowed, in those cases wherever the cost of security was judged too high with respect to advantages introduced. Unauthenticated invocations can be performed without any credentials, neither authentication nor authorization are enforced in these cases. | |
| + | The definition of gCube user not only includes human users, but also services autonomously acting in the system. Batch services (e.g. monitoring services) are an example of such users that, reacting to status changes, or on a temporal basis, interact with other system entities. Thus, some gCube services need to be identified and managed, from the authentication and authorization point of view, as users. | ||
| + | ===Components=== | ||
| − | + | The mechanism currently used in gCube to authenticate service invocatons is the WS-SecureConversation <ref name="WS_SEC_CONV">http://specs.xmlsoap.org/ws/2005/02/sc/WS-SecureConversation.pdf</ref> one. The Java WS-Core container provides a built-in implementation of this standard called GSI-SecureConversation. This choice is mainly driven by the need to delegate caller credentials to the invoked service, as described above. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | Credentials in the gCube infrastructure are managed by the following set of components: | |
| − | + | *'''MyProxy''' - the MyProxy<ref name="MYPROXY">http://grid.ncsa.uiuc.edu/myproxy/</ref> service is in charge of maintaining a delegated short-term copy of user's credentials. The gCube MyProxy configuration allows for storing both credentials issued by IGTF CAs, both for credentials issued by the D4Science CA. In this second case short-lived credentials are generated on the fly for the user, using the MyProxy online CA functionality<ref name="MYPROXY_CA">http://grid.ncsa.uiuc.edu/myproxy/ca/</ref>. | |
| + | *Delegation and CredentialRenewal - Delegation and CredentialRenewal services are in charge to provide gCube services with valid credentials to authenticate theirself in the infrastructure. In fact gCube autonomic behaviour, like that of monitoring processes, and the gCube dynamic deployment functionalities requires credentials to be delegated to services even when the user is offline. This is achieved through the Delegation and CredentialRenewal services, and controlled by a set of predefined delegation policies. For a detailed description of these services you can refer to the [[Virtual Organisation Management]] page. | ||
| − | + | ==Authorization == | |
| + | "Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy. For example, HR staff are normally authorized to access employee records, and this policy is usually formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be granted or rejected."<ref name="WIKI_AUTHZ">http://en.wikipedia.org/wiki/Authorization</ref>. | ||
| − | + | Authorization rights in gCube are modeled basing on the RBAC<ref name="RBAC">http://en.wikipedia.org/wiki/Role-Based_Access_Control</ref> model. In such a model each user must held a role to operate in the gCube infrastructure. In particular authorization policies in the system are defined with respect to roles, that, in turn, are assigned to users. Each resource is then in charge to enforce authorization policies on incoming requests. | |
| + | In distributed multidomain systems the concept of VO is the base to create virtual environments spanning across different administrative domains<ref name="VO_REPORT">http://www.ci.uchicago.edu/events/VirtOrg2008/VO_report.pdf</ref>. gCube architecture mainly aims at enabling Virtual Research Environments, and for this reason Virtual Organizations are a core concept of GCube. In particular, when it comes to authorization, the RBAC model must be merged to the sharing of resources typically enabled by VOs. | ||
| + | ===Model=== | ||
| + | Policies granting access to resources complies with the following gCube VO authorization model. In particular authorisation policies are scope specific, being the scope defined as from the gCube reference model | ||
| + | <ref name="GCUBE_REF_MODEL">https://technical.wiki.d4science.research-infrastructures.eu/documentation/index.php/Reference_Model</ref>. It is worth noticing that the scope introduced in the gCube reference model corresponds to the VO element in the following model. | ||
| − | |||
| + | <center>[[Image:VO_Model.jpg]]</center> | ||
| − | Each | + | Each element in the diagram is briefly introduced below: |
| + | * '''VO''': Each VO in the hierarchy represent a context in which authorization rights can be defined and must be evaluated (Scope). Users and Resources can be included in multiple VOs. Sharing rules can be defined by Resource Managers w.r.t. entire VOs. | ||
| + | * '''User''': Users of the gCube system. This definition includes every service and agent able to autonomously act in the infrastructure. Every user will be univocally identified using a set of user credentials as described in the previous Authentication section. | ||
| + | * '''Resource''': This element represents all gCube resources. Each resource is identified through a resource id. Resources have to belong to a resource type. | ||
| + | * '''ResourceType''': Resource types divides resources in different partitions. Each Resource type is associated to a set of logical operations. These operations can be performed over resources of that type. | ||
| + | * '''Operation''': These are logical operations supported by resources of a given type. Sharing rules and Permissions can be defined using these operations. | ||
| + | * '''Sharing Rule''': Resource Managers can grant VO members access to a given resource defining sharing rules. Sharing rules applies to entire VO, while Permissions applies to roles in a specific VO. | ||
| + | * '''Permission''': Permissions can be defined by VO Managers to grant the right to perform operations to a given role. | ||
| + | * '''Role''': Roles are associated to users in order to give them permissions to execute a set of operations. Role are hierarchical, child roles inherit permissions of parent roles. Hierarchy allows multiple inheritance. Inheritance relationship among roles can be defined only at role creation. | ||
| − | + | Policy enforcement requires resources to contact authorization components, described below, to verify if incoming requests complies with the set of defined policies. The push authorization model is used to enforce authorization for gCube resources<ref name="AUTHZ_MODELS">http://www.ogf.org/documents/GFD.38.pdf</ref>. In such a model a piece of information containing the role assignment, and signed by a trusted identity, is embedded in the client certificate, and send to the service during authentication[<ref name="ATTRIB_CERT">http://www.ietf.org/rfc/rfc3281.txt</ref>]. Resources can thus extract user roles from the received certificate and, knowing the resource id, the scope, and the operation invoked, contact the authorization components to get an authorization decision. | |
| − | + | ||
| − | + | ||
| − | + | ===Components=== | |
| + | Following main elements are part of the gCube authorization architecture: | ||
| − | + | * VOMS - A VOMS<ref name="VOMS">http://grid-auth.infn.it/</ref> server maintains the scope hierarchy as a VOMS groups hierarchy. It is also in charge to store the set of gCube users, as well as their group membership and roles assigned to them. This component is also in charge to sign | |
| + | * Resource Authorization Service - This service is in charge to store authorization policies for gCube resources, i.e. which roles are needed in a given VO to perform an operation on a resource. This component is also in charge of issuing authorization decisions, whenever asked by resources itself. Multiple instances of the authorization service are usually deployed in the infrastructure to avoid bottleneck in policy evaluation. | ||
| − | + | A typical usage scenario for GCube, involving authentication and authorization functionalities is shown in the following diagram. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | <center>[[image:Credentials_Management_Overview.jpg]]</center> | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| + | # When the user logs in the portal, credentials associated with her username/password are retrieved from the MyProxy repository. | ||
| + | # The user is then asked to select the VRE where she wants to operate. The selction triggers the enrichment of user credentials with an attribute certificate signed by the VOMS server. The attribute certificate contains roles held by the user in the current VRE. The credentials obtained are stored in the user session. The user can always change the VRE selection later on; in this case fresh credentials will be generated for the newly selected VRE. | ||
| + | # During the user session, a number of service invocations happens from the portal to backend services. These invocations are performed with user credentials, enriched with user roles, created in the previous step. On the gCube service side the invocation is authenticated, validating user credentials, and authorized, contacting the Resource Authorization Service. Wherever required, user credentials could also be delegated to backend services; this is achieved using the GSI Conversation Delegation functionality. | ||
[[Category:Security]] | [[Category:Security]] | ||
Revision as of 15:35, 13 May 2009
This page describes the overall security model of gCube. Firstly, the authentication handling is introduced, briefly describing the model and components used by gCube to verify user's identity. Secondly, the authorization section gives a brief description of the gCube model, also highlighting main services and components in charge to maintain and enforce authorization policies.
Contents
Authentication
"Authentication is the act of establishing or confirming something (or someone) as authentic, that is, that claims made by or about the subject are true. This might involve confirming the identity of a person, the origins of an artifact, or assuring that a computer program is a trusted one."[1]
Being gCube a distributed system, the authentication process mainly focuses on proving the identity of communicating entities (users, services, hosts, etc.). The aim of gCube authentication is mainly to prevent system usage or damaging by malcious entities.
Delegation
"In numerous applications it is sometimes necessary to "become" some one else, or some other principal in order to take advantage of some privilege(s) they have. Unix systems have had this concept for decades in the su command. With the advent of web based enterprise applications it became clear that something similar was needed for them. That is it became necessary to be able to pass around a set of privileges in some manner. Since privileges are normally associated with a principal (very often a person) the problem became a question of how to pass around these principal's identities and how to allow one system to use that identity to gain access to information on another system."[2]
As from the previous excerpt, identity delegation in gCube is the process of allowing system services and resources to act on user's behalf. This functionality is often required in N-tier large-scale systems, like gCube. An important point to be taken into account when considering delegation is that gCube service can be dynamically deployed in the infrastructure, even if the service administator is not logged in. Even in those cases, valid credentials must be delegated to the deployed service in order to properly operate in the gCube infrastructure.
Model
gCube architecture exploits the Public Key Infrastructure[3] (PKI) paradigm to uniquely identify users in the infrastructure. gCube users are then provided with a set of credentials, i.e. a private key and a public certificate, that are used to for authentication to other entities. Credentials are typically issued and revoked to users by a trusted entity, named Certification Authority (CA). The gCube infrastructure is designed to support CAs acknowledged by the International Grid Trust Federation[4] (IGTF) as well as an infrastructure-specific CA, named "D4Science CA" in the following of this section.
As from the previous, each interaction between entitites, e.g. a service invocation, should be performed in gCube using valid credentials, issued by a trusted Certification Authority (CA).
As far as performances are concerned, security does not come for free. Sometimes the overhead introduced in service invocation by the security handshake can take much longer than the invocation itself, thus excessively penalizing service usability. For this reason also unauthenticated invocatons among gCube entities have been allowed, in those cases wherever the cost of security was judged too high with respect to advantages introduced. Unauthenticated invocations can be performed without any credentials, neither authentication nor authorization are enforced in these cases.
The definition of gCube user not only includes human users, but also services autonomously acting in the system. Batch services (e.g. monitoring services) are an example of such users that, reacting to status changes, or on a temporal basis, interact with other system entities. Thus, some gCube services need to be identified and managed, from the authentication and authorization point of view, as users.
Components
The mechanism currently used in gCube to authenticate service invocatons is the WS-SecureConversation [5] one. The Java WS-Core container provides a built-in implementation of this standard called GSI-SecureConversation. This choice is mainly driven by the need to delegate caller credentials to the invoked service, as described above.
Credentials in the gCube infrastructure are managed by the following set of components:
- MyProxy - the MyProxy[6] service is in charge of maintaining a delegated short-term copy of user's credentials. The gCube MyProxy configuration allows for storing both credentials issued by IGTF CAs, both for credentials issued by the D4Science CA. In this second case short-lived credentials are generated on the fly for the user, using the MyProxy online CA functionality[7].
- Delegation and CredentialRenewal - Delegation and CredentialRenewal services are in charge to provide gCube services with valid credentials to authenticate theirself in the infrastructure. In fact gCube autonomic behaviour, like that of monitoring processes, and the gCube dynamic deployment functionalities requires credentials to be delegated to services even when the user is offline. This is achieved through the Delegation and CredentialRenewal services, and controlled by a set of predefined delegation policies. For a detailed description of these services you can refer to the Virtual Organisation Management page.
Authorization
"Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy. For example, HR staff are normally authorized to access employee records, and this policy is usually formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from (authenticated) consumers shall be granted or rejected."[8].
Authorization rights in gCube are modeled basing on the RBAC[9] model. In such a model each user must held a role to operate in the gCube infrastructure. In particular authorization policies in the system are defined with respect to roles, that, in turn, are assigned to users. Each resource is then in charge to enforce authorization policies on incoming requests.
In distributed multidomain systems the concept of VO is the base to create virtual environments spanning across different administrative domains[10]. gCube architecture mainly aims at enabling Virtual Research Environments, and for this reason Virtual Organizations are a core concept of GCube. In particular, when it comes to authorization, the RBAC model must be merged to the sharing of resources typically enabled by VOs.
Model
Policies granting access to resources complies with the following gCube VO authorization model. In particular authorisation policies are scope specific, being the scope defined as from the gCube reference model [11]. It is worth noticing that the scope introduced in the gCube reference model corresponds to the VO element in the following model.
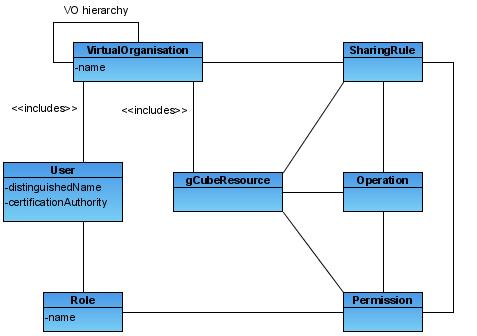
Each element in the diagram is briefly introduced below:
- VO: Each VO in the hierarchy represent a context in which authorization rights can be defined and must be evaluated (Scope). Users and Resources can be included in multiple VOs. Sharing rules can be defined by Resource Managers w.r.t. entire VOs.
- User: Users of the gCube system. This definition includes every service and agent able to autonomously act in the infrastructure. Every user will be univocally identified using a set of user credentials as described in the previous Authentication section.
- Resource: This element represents all gCube resources. Each resource is identified through a resource id. Resources have to belong to a resource type.
- ResourceType: Resource types divides resources in different partitions. Each Resource type is associated to a set of logical operations. These operations can be performed over resources of that type.
- Operation: These are logical operations supported by resources of a given type. Sharing rules and Permissions can be defined using these operations.
- Sharing Rule: Resource Managers can grant VO members access to a given resource defining sharing rules. Sharing rules applies to entire VO, while Permissions applies to roles in a specific VO.
- Permission: Permissions can be defined by VO Managers to grant the right to perform operations to a given role.
- Role: Roles are associated to users in order to give them permissions to execute a set of operations. Role are hierarchical, child roles inherit permissions of parent roles. Hierarchy allows multiple inheritance. Inheritance relationship among roles can be defined only at role creation.
Policy enforcement requires resources to contact authorization components, described below, to verify if incoming requests complies with the set of defined policies. The push authorization model is used to enforce authorization for gCube resources[12]. In such a model a piece of information containing the role assignment, and signed by a trusted identity, is embedded in the client certificate, and send to the service during authentication[[13]]. Resources can thus extract user roles from the received certificate and, knowing the resource id, the scope, and the operation invoked, contact the authorization components to get an authorization decision.
Components
Following main elements are part of the gCube authorization architecture:
- VOMS - A VOMS[14] server maintains the scope hierarchy as a VOMS groups hierarchy. It is also in charge to store the set of gCube users, as well as their group membership and roles assigned to them. This component is also in charge to sign
- Resource Authorization Service - This service is in charge to store authorization policies for gCube resources, i.e. which roles are needed in a given VO to perform an operation on a resource. This component is also in charge of issuing authorization decisions, whenever asked by resources itself. Multiple instances of the authorization service are usually deployed in the infrastructure to avoid bottleneck in policy evaluation.
A typical usage scenario for GCube, involving authentication and authorization functionalities is shown in the following diagram.
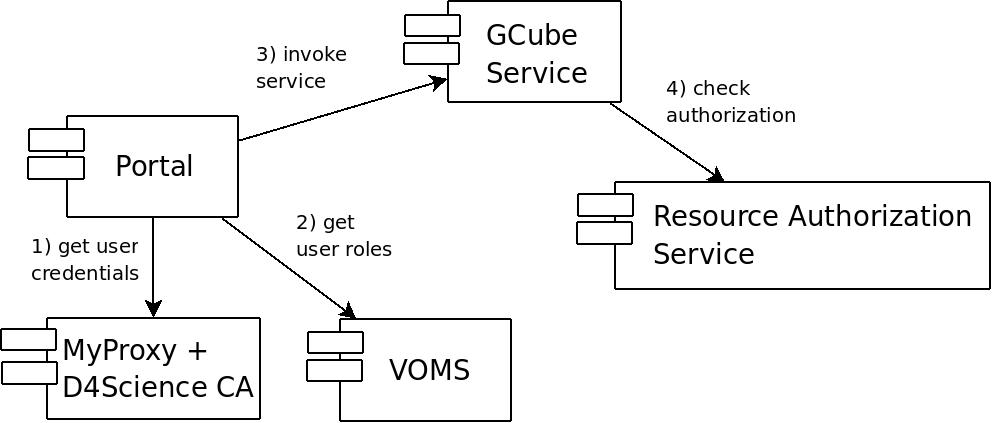
- When the user logs in the portal, credentials associated with her username/password are retrieved from the MyProxy repository.
- The user is then asked to select the VRE where she wants to operate. The selction triggers the enrichment of user credentials with an attribute certificate signed by the VOMS server. The attribute certificate contains roles held by the user in the current VRE. The credentials obtained are stored in the user session. The user can always change the VRE selection later on; in this case fresh credentials will be generated for the newly selected VRE.
- During the user session, a number of service invocations happens from the portal to backend services. These invocations are performed with user credentials, enriched with user roles, created in the previous step. On the gCube service side the invocation is authenticated, validating user credentials, and authorized, contacting the Resource Authorization Service. Wherever required, user credentials could also be delegated to backend services; this is achieved using the GSI Conversation Delegation functionality.